In our previous articles we have discussed Cryptography, Symmetric, Asymmetric encryption, and related things. In this edition, we will be deeply focusing on Threshold signature Schemes, multi-signature and multi-party computations.
Let assume Bob has something secret in his account and needs to keep it secure. Now in scenario1, he put that into a digital vault, with one key. In scenario two, he generated multiple keys using different cryptographic techniques and shared with 4 of his friends. Now which one is more secure and no single point of failure?
Definitely the one, with multi-parties involved and multi-signatures required. Now do all his friends needs to sign together to unlock the fund, how the entire system can be set up, so that we can avoid one single point of failure, neither during the time of key generation, nor during the time of signing the transactions.
Let’s sit for the next couple of minutes and understand how we can help Bob achieving his goal.
What are Threshold Signature Schemes?
As the name implies, Threshold means there will be a specific benchmark to signing transactions and that’s what Threshold Signature Scheme does. It sets a limit of participants who jointly share the part of the private keys to sign the transactions. Only if all the shares of the private keys are collectively joined , the transaction becomes valid, else it will get rejected. Hence eliminating any forthcoming Mt.Gox like events from happening and putting the crypto space in thaw.
To put that into perspective, let’s look at examples demonstrated in the how TSS work section.
How Does the Threshold Signature Scheme Work?
By now, you have understood that under the Threshold Signature Scheme, there’s MPC or Multi-Party Computation to sign transactions. Which boils down to many people involved in the KeyGen and Sign algorithm. We shall demonstrate the same via an example. As mentioned above in the introduction, lets assume that scenario again and see how Bob can do this.
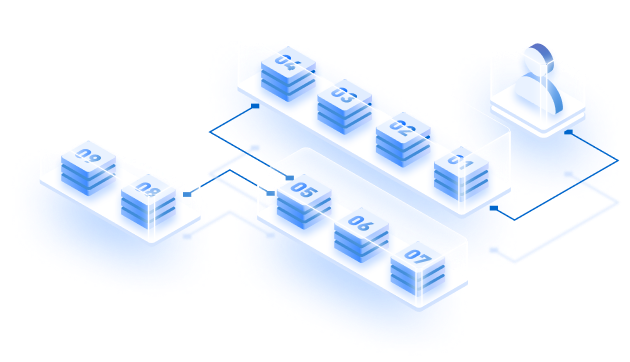
Bob is using TSS where he has predefined that for the transaction to become valid, it must be supported by “T of n” where ‘n’ number is the number of members among ‘T’, and T is the minimum number required to make the transaction valid. Suppose, there are 7 people in the TSS, out of that, if 4 people share their key share, as decided previously as threshold, the transaction will be deemed as valid and binding if 4 people sign the transaction.

But, the catch here is that all the 4 people need not have to send their private-key to a single location and sign the transaction. On the contrary, as mentioned in the image above, you can see in the left-side of the image under MPC that there are multiple people involved in the key-signing mechanism. Every participating individual shall input their private keys which are subject to change after a specific expiration period. Hence, there’s no single point of failure, neither the key generation occurs from a single source which can be corrupted. In this way, it protects the entire key signing process.
Benefits of Threshold Signature Scheme
Enhanced Security
Since the key generation process is distributed and there’s no single point of key generation and key signing, possibilities of failure: internal or external can be prevented easily.
Transaction Sizes are Smaller on TSS
For Threshold Signature Scheme, transaction sizes are smaller or equivalent in comparison to a normal signature despite providing very high security and throughput. Hence you have to incur lower costs while getting them validated.
Easy Key Share Research
In a Threshold Signature Scheme, unlike in multisig where you have continuously interacted with the smart-contract for changing the keys, there’s no such requirement. You can generate different key-pairs off-chain without the need to interact with the smart-contract for upgrading the keys.
Better Operational Flexibility
When you are using the TSS, the complete private keys are not disclosed to the participating members. As a result, you can easily share the fragments of the keys to the new members without the need to change the complete key time and again to safeguard it. In this way, it always gives you better operational flexibility in comparison to multi-sig
Is TSS Better Than Multisig or Shamir Secret Sharing Scheme?

TSS and Multisig are both methods used in blockchain systems to distribute control among multiple participants. However, they differ in how they achieve this goal and where they operate within the blockchain.
TSS operates off-chain, meaning it uses cryptographic techniques outside the blockchain to distribute the power of signing transactions among multiple parties. The signers’ information is combined into a regular-looking transaction, ensuring privacy and reducing costs. TSS can be implemented in any system that supports cryptography, making it versatile and independent of any specific blockchain.
Multisig, on the other hand, operates on-chain. It directly encodes the multi-signature functionality into the blockchain software or smart contracts. However, this approach can compromise privacy since the number of signers is exposed on the blockchain. Additionally, the communication of information about the different signers increases the cost of multisig transactions.
Moving on to Shamir’s Secret Sharing Scheme (SSSS), it also distributes a secret among multiple parties. However, in SSSS, a single party called the “dealer” generates the secret shares and distributes them to different locations. To perform a signature, the parties must reconstruct the full private key, which can introduce a single point of failure during each signing operation.
In contrast, TSS eliminates the need for a dealer and distributes the role among multiple parties. The private key is never generated at a single location, enhancing security. Furthermore, TSS enables distributed signing without reconstructing the secret shares, reducing the risk of single points of failure during the signing process.
Overall, TSS provides a way to achieve multi-signature functionality while maintaining privacy and reducing costs off-chain. It can be implemented in various systems through cryptography. On the other hand, Shamir’s Secret Sharing Scheme distributes the private key among multiple locations but requires key reconstruction for signing, which can introduce vulnerabilities. Multisig operates on-chain, encoding multi-signature functionality into the blockchain but may compromise privacy and incur higher costs due to the communication of signers’ information.
Is there any risk involved in Threshold Signature Scheme?
Threshold Signature Scheme is new and its efficacies are yet to surface which shall happen only with time. Attackers, at the moment, are trying out new attack vectors to compromise the wallets running under the TSS scheme. As a result , the need for an additional security layer to safeguard the key management system also arises which will surely occur as the technology matures.
To put the threat into perspective, let us suppose that there are two business entities which are planning to sign the documents. As implied, any interaction with the members of the consortium will not cause an issue.
But there might be some data which requires a third-party validation. It shall expose the point of failure. For example, t-participants or number of authorized participants of the verifying group shall create a session key and compute the data. T-members of the other groups can verify the transaction by keeping a designated verifier in their confidence and coercing him/her into signing a wrongful transaction.
At this point, the efficacy has been contested and it shall become public only with time when certain challenges surface and TSS is able to build on top of that to solve those problems. At present, Threshold Signature Scheme is undoubtedly much safer than multi-sig until and unless we get exposed to multiple points of failure.
Conclusion
In conclusion, for the true adoption of blockchain technology to take place, it is crucial that enterprises do not face unnecessary struggles while utilizing the technology. In this article, we have provided an introduction to the threshold signature scheme, a captivating cryptographic primitive that has the potential to revolutionize the way we employ blockchain. In future series, we will delve into other aspects of cryptography, such as end-to-end encryption, as well as explore various other topics.
Building something around Blockchain? Need support on Blockchain infrastructure, nodes, APIs, decentralized storage? Visit Zeeve, and start your blockchain journey today.