Successful adoption of any technology is dependent upon security compliance and risk. Doesn’t matter what the technology is, security remains paramount. The blockchain paradigm is tamper-proof but not immune to hacks and security challenges. Monitoring the blockchain ecosystem is equally important as it is for other technologies. The cybersecurity measures apply to the blockchain as well.
Furthermore, security becomes of utmost importance when working with big industries such as healthcare, finance, supply chain, and many more. Blockchain technology is secure, no doubt, but there are many issues that surface. There are many problems, such as regulatory compliance and data confidentiality.
Notorious Hackers can find a flaw in the system and cause a loss of millions, if not billions. The DAO hack was one such example. Even in the DAO hack, there was so much confusion and a lack of policies, that an ad-hoc committee was established much later. Thus, it becomes necessary for organizations to understand the security system of blockchain. In this blog, we will highlight more on blockchain security and compliance and how it can be managed.
How the Security differs in Blockchain types
In order to build a successful blockchain application, you must determine which type of network is most appropriate for your enterprise. Blockchain networks are either public or private, which determines who can participate. Moreover, access to the networks is permissioned or permissionless, based on the way participants gain access to them.
Regarding reliability, private and permissioned networks are preferred for better security and compliance. In terms of compliance and regulation, private and permissioned networks are desirable. Decentralization and distribution can, however, be accomplished more effortlessly with public and permissionless networks.
The three pillars of blockchain security are:
- Confidentiality
- Data integrity
- Availability of data
In the case of enterprise-grade solutions, there are a lot of legacy systems, and the input to the smart contract system is external. Ultimately, it’s necessary to ensure that blockchain security and compliance frameworks are analyzed well, as technologies are changing fast.
— Ghan Vashistha, CTO & Co-founder, Zeeve
You can watch Zeeve’s youtube session and understand in a better way about blockchain security and compliance.
The Four Types of Blockchain Security Attacks
Phishing Attacks
The attack is a way to get information about the individual. Wallet key owners receive emails that appear to come from an authorised source but are actually deceptive. Using fake hyperlinks, the emails request the end users for their credentials. This causes a loss for the users and of course for the blockchain network.
Routing Attacks
In routing attacks, hackers seize the data when it is being transferred to and for from the internet service providers. The hackers split the blockchain network into separate parts and block the communication channel. The attacker’s newly formed chains are discontinued once the attack is complete.
Sybil Attacks
A Sybil attack involves hackers creating and using many false network identities in order to overload the network and crash it. The node in a network has multiple active identities. The identities aim to gain majority power over the chain. The fake identities seem real to the outsiders making the system more vulnerable as it becomes difficult to find fault.
51% Attacks
51% attacks are attained by renting minting hash from a third party. On a blockchain network when the mining power is exceeding 50% for a miner or group of miners. It is considered to control the network if you hold more than 50% of the power. While the likelihood of a 51% attack is relatively less, it isn’t completely to be ignored.
Key Features of Security Software
Some of the key features of using security software for blockchain-compliant networks are:
Investigation and Monitoring
It is a feature that allows users to examine digital currency transactions. There is an automatic route detection to track transactions. The investigation and monitoring also involve risk assessment and further assign ratings.
Knowing Your Transactions (KYT)
With KYT, you can quickly analyze and investigate transactions. Besides providing information on blockchain addresses, KYT also includes information on their true identities. KYT does a critical analysis of the enterprise blockchain to identify fraudulent transactions.
Navigation Assistance
You gain consistent and precise knowledge of the source and destination of money with navigation assistance, which provides strong traceability and adjustable risk rules. The navigation assistance traces the blockchain path flow.
Virtual Asset Service Provider (VASP)
VASP monitors risk and ensures regulatory compliance. The VASP is essential when it comes to exchanges occurring between virtual assets. VASP helps you to become blockchain compliant as it verifies identity, tracks crypto activities, and enables law enforcement and regulations.
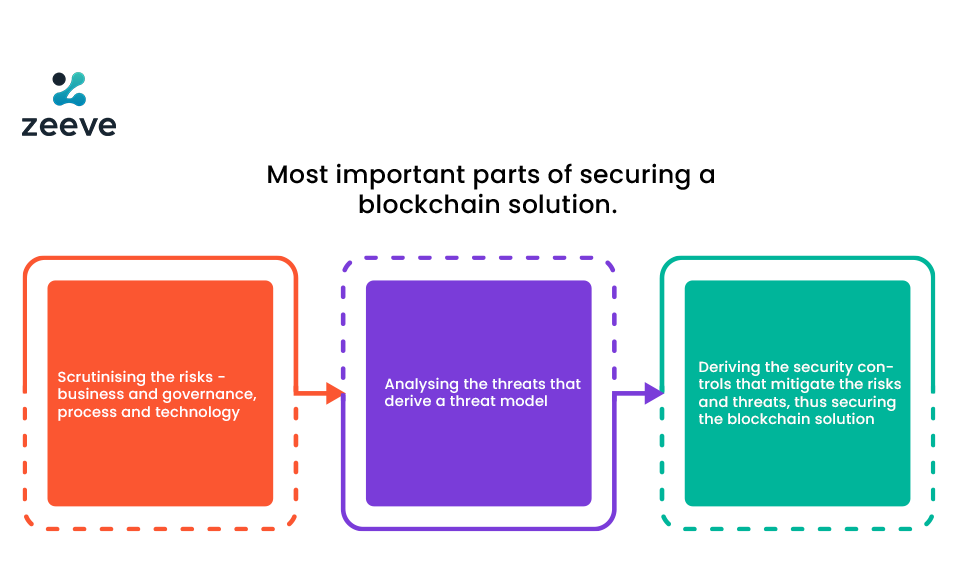
A few Questions that assist in Blockchain Security and Compliance
Security starts with understanding your type of blockchain implemented mostly permissionless or private. Nowadays, because of side chains evolving the private and public. Here is the set of important questions we define while defining a blockchain solution
In each block, what data will be recorded?
The blocks on the network contain information on the previous block, transaction data, and timestamp data. The data remains secure through the usage of cryptography. Depending upon the governance model of a blockchain the data is stored and security is taken care of.
What is the governance model for participating organizations?
Security governance becomes very important in the corporate setting. Security governance becomes challenging in the decentralized system. The governance models in an enterprise decide on many factors. It is essential to understand the consensus mechanism, and blockchain types such as public, private, etc. and there has to be an understanding of the node vetting process. The updation of the core code, or the application of a security patch. All is being controlled by the governance model.
Are there any relevant regulatory requirements, and how can they be confronted?
Regulatory requirements are mostly industry-specific. It is vital to design the network in a way that the private information remains secure or gets deleted after the requirement is over. There will be the usage of pseudonym identifiers. Further, the regulation becomes better through the usage of zero-knowledge proofs.
How are the attributes of identity managed? How are the keys managed and dismissed?
The user on the blockchain network has a private key to sign the transactions digitally. The key management approach is that the keys are stored in the local storage and can be accessed by the blockchain network’s software. Subsequently, there is multi-factor authentication for security. The public key infrastructure is there to protect the data as well.
For blockchain participants, what is the disaster recovery plan?
Communicating the attack on time and understanding the minimal security status for blockchain clients for participation. The further recovery process is time-taking, the blockchain employs cryptography makes it more secure — however, complementary controls need to be integrated to make the network more secure.
What is the way to resolve blockchain networks’ block collisions?
Block collisions are the ones that happen when there is double spending. To know more about the block and transactions, the full nodes come to be helpful. Blockchain innovation relies heavily on cryptographic hash functions. In essence, the hash gives processed transactions security capabilities, making them immutable.
Solutions to Manage Security & Compliance
Administrators must determine the security controls that lessen the risks and threats based on the following ways
The platforms need to develop a risk model that can address all business, governance, technology, and process risks. It is vital to enforce security commands that are exclusive to the blockchain network’s type. A blockchain platform will apply conventional security controls and enforce business controls for blockchain.
Encryption of key, a blockchain management platform would provide key management service in which the private keys are stored safely. There should be node backup to initiate on-demand or scheduled backups.
Along with the multi-factor authentication for secure blockchain network connectivity, one practice can be implemented. That is data minimization. Data minimization is keeping crucial data off-chain and allowing minimal data on-chain.
Finally, it is also critical to examine the resilience requirements for a blockchain system. This includes the tamper-resistant hardware and secures key backup environment. Companies need to monitor cryptoanalysis. Otherwise, it can have a negative impact on their systems.
Features integral to blockchain monitoring and how Zeeve helps
All users should incorporate the following critical aspects of monitoring into their blockchain environments:
1. Looking out for and tackling suspicious behaviour: The top priority for blockchain teams should be to recognize and address any suspicious activity. As large-scale implementations involve millions or even billions of dollars in transactions each day, it is essential to monitor these transactions and guarantee their authenticity. Users should be aware of events such as an increase in failed transactions, alterations to access controls and permissions, multiple unsuccessful login attempts, unauthorized new users, sudden increases or decreases in transaction volume, and transactions that take place outside of regular business hours.
2. Receiving real-time alerts for critical issues: Zeeve offers real-time notifications to help detect and investigate any potential issues that could arise, thereby reducing the risk of a single malicious actor compromising the security of the blockchain. Automated alerting should be an integral part of any blockchain implementation in order to ensure the safety and integrity of the network.
3. Setting up and making auditable records accessible: In order to ensure the validity of transactions and provide an audit trail, Zeeve creates auditable records that can be accessed by auditors. These records are designed to protect the privacy of the data while still providing an understandable record for auditors to assess. In order to guarantee the accuracy and integrity of the data, users should incorporate the necessary monitoring components into their blockchain systems.
4. Allowing complete analysis of the blockchain data and events: Zeeve offers users a comprehensive overview of blockchain data and events, providing them with essential information such as transaction volume, contract utilization, validation speeds, and overall chain health. With this information, users can gain a better understanding of the blockchain and make informed decisions.
5. Strengthening the security and health of the blockchain nodes and networks: Zeeve offers tools to monitor the functioning of blockchain networks and guarantee their stability. These include dashboards and reports to investigate and identify problems related to asset stock, contract application, transaction numbers, validation speeds, node health, and more. Furthermore, users can authenticate and approve blockchain transactions to give all blockchain users the assurance that the endorsed transactions are accurate and valid.
Summing it all Up
It is vital to safeguard enterprises and organizations from various fraudulent activities. The blockchain needs to be scrutinized more in the coming years as the technology is going to be adopted to a greater extent. For long-term viability, blockchain security monitoring and compliance services will be helpful for an organization.
With appropriate security management, the infiltration in the ecosystem reduces to much extent. The existing challenges can be removed using correct mitigation strategies and partnering with a blockchain platform with accurate information about the blockchain system and its challenges. There should be more training for professionals, frequent code reviews, patching, and data integrity checks.
Partner With Zeeve
Do you want to avert blockchain risks for your enterprise? The clouds of confusion will wane off if you partner with Zeeve.
As the leading Blockchain Infrastructure Management Platform, we believe in enterprises having the best efficiency and robust security and compliance. We are trusted by Blockchain Startups, Enterprises, and Web 3.0 Developers across the world. You will be able to learn more about our work through Twitter and Telegram, so do follow us. Have a question in mind? Feel free to connect on call.